Preemptive Security: Today’s cybersecurity paradigm shift has arrived.

Gartner says that in the age of GenAI, “preemptive capabilities, not detection and response, are the future of cybersecurity.” That’s not just a trend; it’s a forecast backed by measurable change in how security investments are being prioritized globally. By 2030, preemptive cybersecurity solutions are expected to account for over 50% of IT security spending, replacing standalone detection and response solutions as the preferred defense against evolving threats. (Gartner)
At Ridgeback, we’ve built our platform with this preemptive philosophy at its core as a foundational design principle around Deny, Deceive and Disrupt - so compromise doesn’t happen.
- We don’t wait to correlate alerts and then react.
- We anticipate adversary intent and neutralize threats as they manifest.
- We focus our customers on proactive containment, not reactive triage.
Gartner also makes a critical point that “preemptive cybersecurity will soon be the new gold standard for every entity operating on, in, or through the various interconnected layers of the global attack surface grid (GASG).” (Gartner)
This affirmation from the leading technology research firm underscores what Ridgeback customers already experience:
Security that anticipates, not assesses.
Gartner cites the need for a new generation of preemptive security tools. Ridgeback is the leader in applying the Gartner standards of “deny, deceive and disrupt” to cybersecurity. If you’re ready to move beyond legacy detection-and-response toward truly preemptive defense, let’s talk about what that means in practice.
Ridgeback: Active Defense for Modern Threats
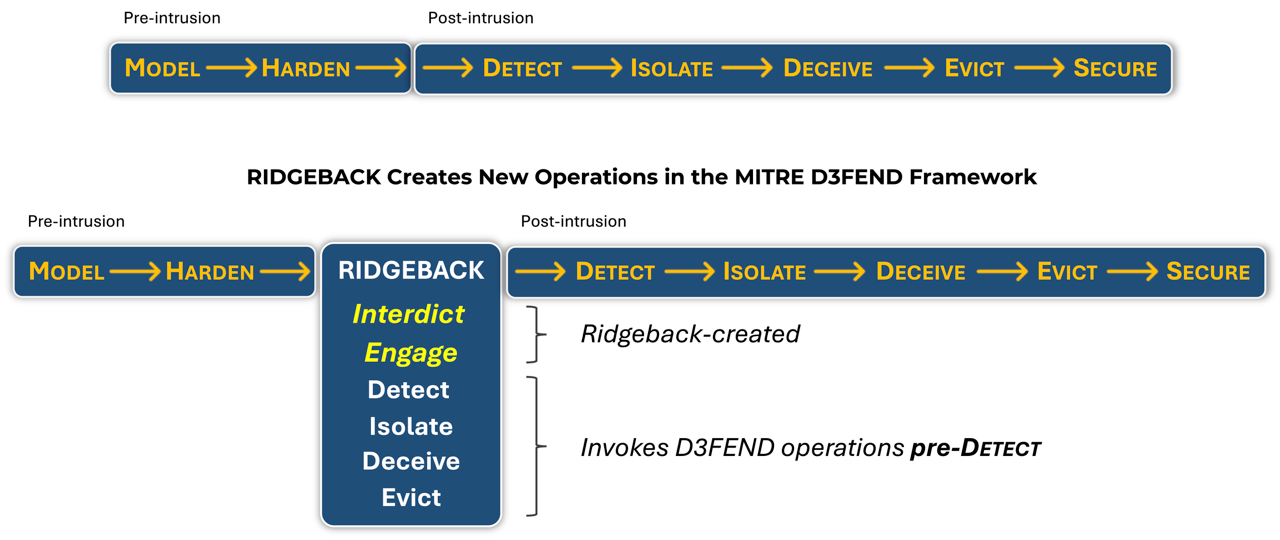
In the age of AI-driven attacks, security effectiveness is no longer measured by how fast you respond, but by whether the attack ever succeeds at all. Ridgeback delivers preemptive security that anticipates and disrupts adversaries before damage occurs. By shifting left of detect, Ridgeback moves critical defensive action earlier in the security lifecycle by inserting real-time interdiction and engagement directly into the attack path rather than waiting for alerts after compromise. Designed to deploy easily into any environment, from global enterprises to small, resource-constrained organizations, Ridgeback transforms security from reactive containment into proactive control.
Deploy Anywhere. Defend Everywhere.
Rapid Deployment and Operational Ease
Ridgeback is designed for immediate utility, requiring no agents on endpoints and minimal ongoing administration.
Comprehensive Network Visibility
Achieve 100% visibility across all network layers and device types without requiring complex routing changes.
Efficiency in Complex Systems
Ridgeback helps IT and security teams transform chaotic environments into orderly systems, drastically reducing the time required to identify issues and contain threats.
High-Fidelity Sensing
By focusing on actual adversary interaction rather than mere inference, Ridgeback delivers high-fidelity signals with virtually no false positives.
Automated Containment and Disruption
Ridgeback imposes high costs on attackers by presenting Phantom on-the-fly, on-demand to engage, discover, and halt lateral movement.
Compliance and Control Validation
Meet regulatory requirements and validate Zero Trust architectures through continuous, real-time evidence production.
Business and Financial Impact
Beyond security, Ridgeback optimizes your operations by saving analyst hours and de-emphasizing redundant tools.
The Active Defense Advantage
Ridgeback fills the blind spots created by traditional EDR, NDR, and UBA solutions, providing instant containment at the network layer.

