Never bring a knife to a gunfight, and definitely…
DON’T BRING AFTER-THE-FACT DETECTION TO A REAL-TIME CYBERWAR
Why Offense for Defense?
Even the most advanced ‘detect-and-respond’ solutions that leverage AI to do their work leave defenders on the backfoot, playing a reactive game of catch up. Automated attacks need automated solutions.
Ridgeback uses offensive techniques scaled and automated for defense to engage and impair adversary operations in actual real-time autonomously.
With Ridgeback’s offense-for-defense in place attackers won’t be interested in exploiting your network…they’ll find an easier target to victimize.
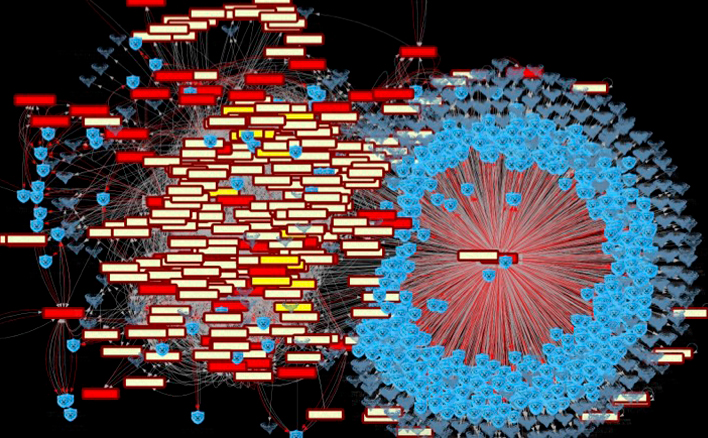
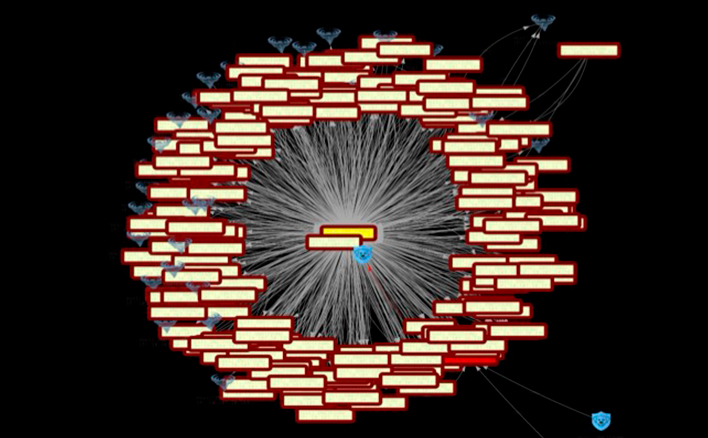
Render order from chaos with true enterprise-wide situational awareness.
Unlike common network mapping and data flow tools, Ridgeback instantly and quietly captures, reports and visualizes the entire network – including all IT, OT, IoT – in motion real-time, 24/7. Ridgeback will pinpoint opportunities not observed by other tools to reform network chaos for efficiency, resilience and security.
Some of the ways your IT and security peers use Ridgeback...
What’s driving risk in your systems?
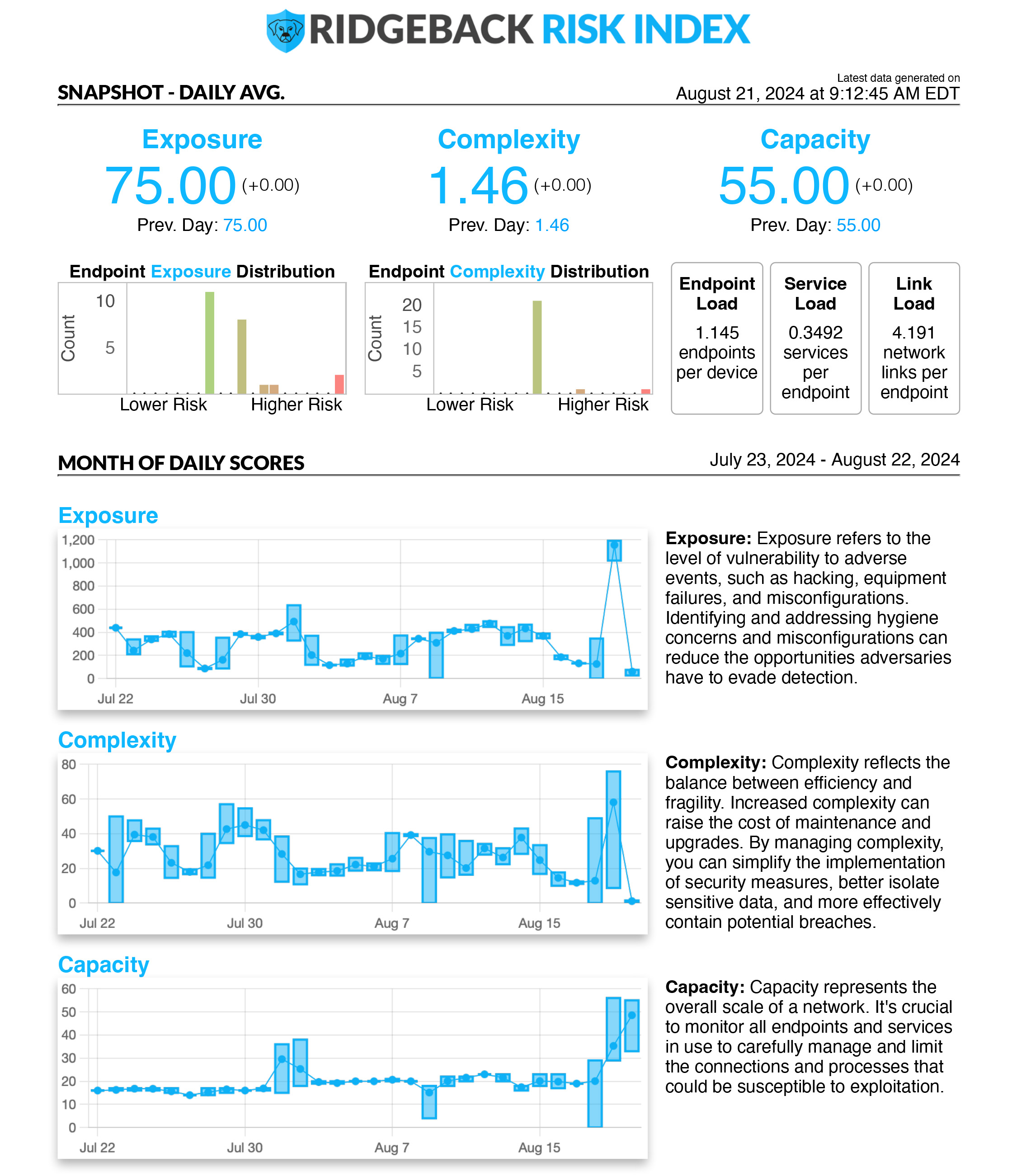
- See your network’s risk factors on demand: hourly, daily, and weekly scores.
- Empower collaboration between tech and non-tech teams, all the way up to the board of directors.
- Gain a precise understanding of how to fortify your network and confidently navigate the impacts of IT and security implementations.
- Higher scores indicate more work, expense, weaker resiliency, and more vulnerability to exploitation.
Empowering Leadership with True Real-time Security Insights
Whether you manage a company or a corporation or are responsible for a balance sheet as a financial officer, there are important ways to understand the value of Ridgeback via capabilities not available anywhere else.
Making things easy is table stakes for innovators. All these capabilities come with an easy, instant-on deployment model that defies conventional thinking about implementing demanding, big data solutions.
Is Ridgeback right for you?
Almost certainly, yes. Ridgeback is designed for versatility, allowing it to integrate seamlessly with nearly any security strategy.
Once they start using it, we see people rapidly go from "Ridgeback is cool" to "Ridgeback is an essential part of our infrastructure."
Whether you are protecting and managing information technology (IT) or operational technology (OT), you will find numerous ways in which Ridgeback helps you secure and manage your assets.