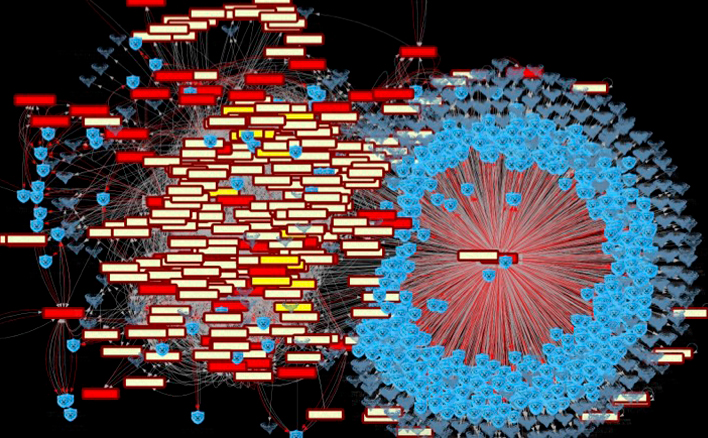
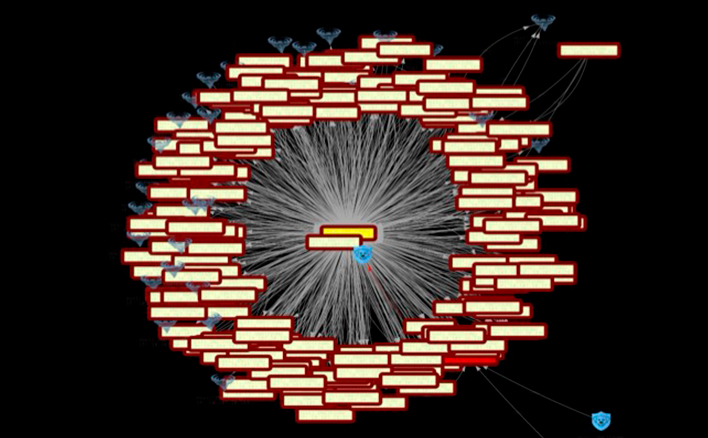
Some of the ways your peers use Ridgeback...
Is Ridgeback right for you?
Almost certainly, yes. Ridgeback is designed for versatility, allowing it to integrate seamlessly with nearly any security strategy.
Once they start using it, we see people rapidly go from "Ridgeback is cool" to "Ridgeback is an essential part of our infrastructure."
Whether you are protecting and managing information technology (IT) or operational technology (OT), you will find numerous ways in which Ridgeback helps you secure and manage your assets.
Empowering Leadership with Key Technology Insights
Whether you manage a company or a corporation or are responsible for a balance sheet as a financial officer, there are important ways to understand the value of Ridgeback via capabilities not available anywhere else.
Making things easy is table stakes for innovators. All these capabilities come with an easy, instant-on deployment model that defies conventional thinking about implementing demanding, big data solutions.