AI-enabled cyber-attacks are fast.
Ridgeback's Preemptive Defense is faster.
“Preemptive capabilities — not detection and response — are the future of cybersecurity in the age of GenAI.” (Gartner)
Automated Attacks Need Preemptive Defenses
In the age of GenAI, threats evolve faster than Traditional detection-and-response defenses can keep up. (As recognized by Gartner’s September 2025 cybersecurity forecast.) Ridgeback implements preemptive cybersecurity: using predictive threat insights and real-time interaction to neutralize threats before they execute. By shifting from passive defense to active deterrence, Ridgeback compels attackers to seek easier victims.
Read the scholarship behind Ridgeback's Preemptive Defense in the DoD’s Cyber Defense Review HERE
The article explains that today’s cyber threats to critical infrastructure are so advanced that traditional security defenses alone are no longer enough. Fogarty presents the “Sword of Damocles” idea, which focuses on constant visibility and the ability to hold attackers at risk as a way to discourage attacks. He argues that cybersecurity should shift from just blocking threats to actively changing how attackers think and behave. (Read More)
References
Fogarty, S. C. (2025). The sword of Damocles: A cybersecurity paradigm shift for the defense of critical infrastructure. The Cyber Defense Review, 10(1), 29–39. https://doi.org/10.55682/cdr/kpwx-q1q1
Reactive Chaos or Preemptive Order?
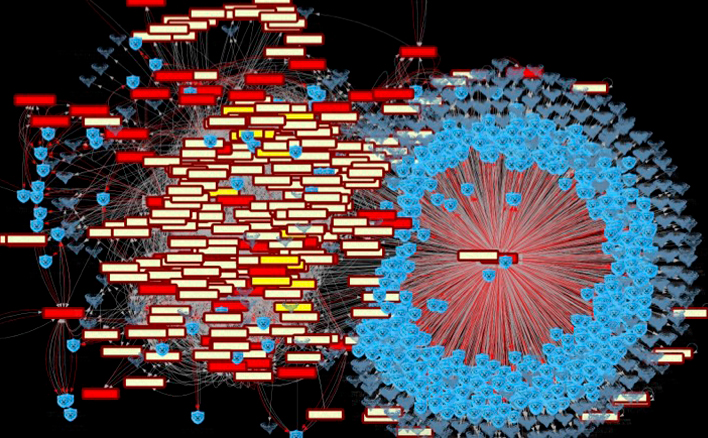
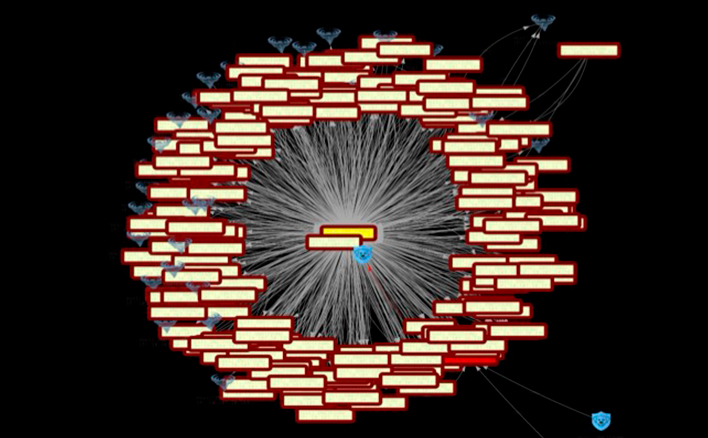
Ridgeback does not infer network behavior from log files, telemetry exports, or delayed analytics. It presents network operating data directly, as activity occurs. This direct view of how the network actually operates exposes inefficiencies, misconfigurations, and risk conditions that log-based tools cannot see.
Some of the ways your IT and security peers use Ridgeback...
What’s driving risk in your systems?
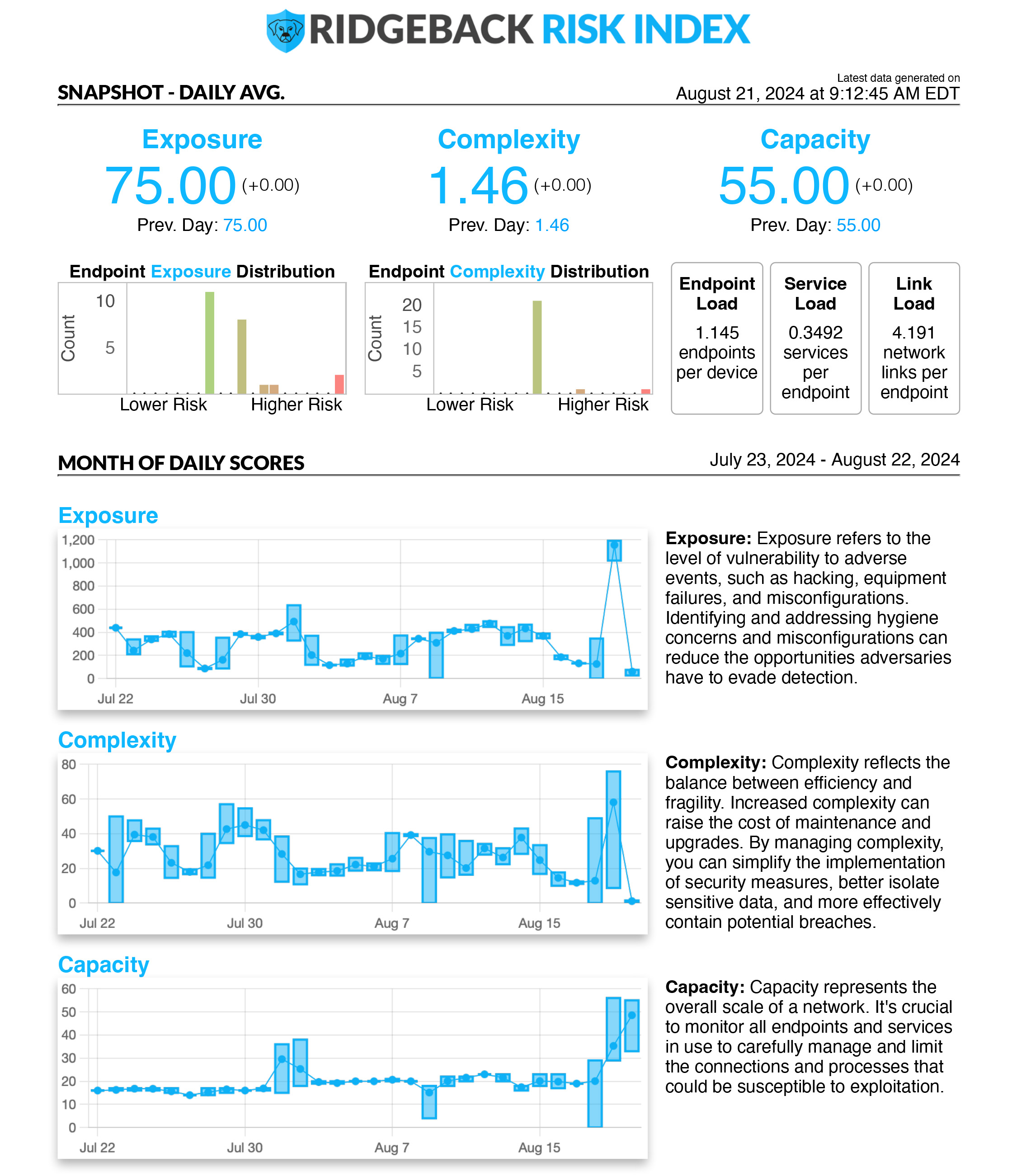
- See your network’s risk factors on demand: hourly, daily, and weekly scores.
- Empower collaboration between tech and non-tech teams, all the way up to the board of directors.
- Gain a precise understanding of how to fortify your network and confidently navigate the impacts of IT and security implementations.
- Higher scores indicate more work, expense, weaker resiliency, and more vulnerability to exploitation.